A gaggle of Bitcoin Core builders mentioned quite a lot of assault vectors for Bitcoin in addition to techniques to devise forward and circumvent nefarious actors.
A gaggle of Bitcoin Core builders mentioned quite a lot of assault vectors for Bitcoin in addition to techniques to devise forward and circumvent nefarious actors.
Bitcoin 2022, hosted in Miami, Florida, on April 6-9, featured a panel titled “Preventing Attacks on Bitcoin” with 3 Bitcoin Core builders: Luke Dashjr, Bryan Bishop and Jameson Lopp (substituting for Peter Todd). The panel was once moderated by way of Shinobi.
The panelists speak about technical and social assault vectors, basically within the building means of Bitcoin Core, that might obstruct or wholly derail Bitcoin’s sole venture as immutable cash. The aim for overtly brainstorming assault vectors is to formulate suitable protection measures and, as Sun Tzu’s “The Artwork of Conflict” strategizes:
“Don’t consider that the enemy isn’t coming. Believe your readiness to fulfill him. Don’t consider that the enemy gained’t assault. Depend most effective in your talent to select a spot that the enemy can’t assault.”
The next is a abstract of mentioned panel with a snappy evaluation of the Bitcoin Core building procedure.
Transient Bitcoin Core Evaluate
The Bitcoin Core builders paintings thru a building procedure to provide the Bitcoin protocol malicious program patches, tool optimizations and enhanced options; they then submit those updates following neighborhood consensus by the use of Bitcoin Improvement Proposals (BIPs). To effectively engineer an assault towards the improvement procedure, on both a technical or social degree, would doubtlessly obstruct (infrequently crucial) protocol updates and instill mistrust between builders.
To elucidate, Bitcoin Core is a loose and open-source tool implementation of a Bitcoin full node, known as a consumer. Even though deceptive in title, Bitcoin Core does now not have centralized or “core” regulate over the Bitcoin community, however somewhat serves as only one imaginable consumer that persons are loose to make use of at their discretion. As nicely, the Bitcoin protocol consensus laws require that each one Bitcoin complete nodes and financial individuals unfailingly put in force the ones laws when making an allowance for the validity of a block.
Moreover, Bitcoin Core updates aren’t downloaded mechanically however somewhat manually, as computerized tool updates supply an assault vector for a mischievous actor to compromise all of the nodes and miners in one stroke.
The Bitcoin Core crew of builders don’t pedestal a unmarried chief or spokesperson — thus distancing the buyer and building procedure from private personality exploitation because of faults all earthly leaders inherently possess. For instance, narcissistic leaders will also be weakened by way of developing unrest inside their fan base, or short-tempered leaders can behave irrationally when provoked with insults. To overturn an upstart motion, one should cleverly put off its chief or fracture their following.
But with out a unmarried chief, how do impartial Bitcoin Core builders come to settlement on complicated design alternatives or emergency malicious program fixes? The aforementioned BIPs are used within the Bitcoin Core building procedure to put into effect options or knowledge to the Bitcoin protocol, however BIPs additionally paintings to standardize the verbal exchange of recent concepts, as diagrammatically depicted under and as described in BIP 1:
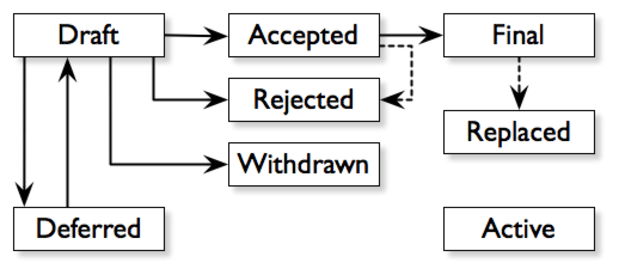
How are we able to throw a wrench into this procedure? Regardless of introducing some formality by the use of BIP 1 into an in a different way unstructured community, there gifts a chance for malicious or just faulty actors to subvert the improvement procedure thru each technical and social approach. Spotting this “wrench” then again is incessantly most effective imaginable in hindsight — ensuring assault vectors particularly tricky to come across and steer clear of. If you’ll dodge a wrench, you’ll dodge a deviant developer hell-bent on pushing their self-serving time table at Bitcoin’s expense.
In apply, precise BIP implementations aren’t as neat as a workflow diagram and the above rationalization has been abridged. On the other hand, we will start to theorize nefarious find out how to subvert the decentralized building procedure.
Word: The time period “consensus” is an ambiguous phrase used to suggest a number of various things past the foundations of Bitcoin. Generally used to suggest “everybody mainly is of the same opinion” on a choice whilst, if truth be told, there are extra correct, distinct phrases that paintings to higher outline the various ranges of settlement on a choice than the catch-all time period “consensus.” For simplicity’s sake, this text refers to near-unanimous and common settlement as attaining “consensus.”
Former Assaults On Bitcoin
The Bitcoin community deployed in 2009 with a number of crucial bugs and oversights that can have led to critical technical assault vectors, however the ones publicly-known vulnerabilities have been remedied way back. Normally talking, those insects and oversights are arduous to seek out as there may be not anything within the code this is obtrusively or painfully glaring. A devoted open-source building neighborhood voluntarily contributing to the codebase has worked incessantly to make stronger the protocol’s integrity during the last decade after which some. Through figuring out previous vulnerabilities and their answers, we will stay vigilant in mitigating long term flaws and supply a foundation for producing worst-case eventualities to seek for attainable protection mechanisms.
Undoubtedly essentially the most notable social assault at the Bitcoin neighborhood and building procedure took place in 2015 when two well-respected and veteran Bitcoin builders at the moment, Gavin Andresen and Mike Hearn, created and promoted a brand new, incompatible Bitcoin consumer categorized Bitcoin XT. Bitcoin XT proposed expanding the imaginable transactions in line with block, referred to as the blocksize, as a method of competing with standard fee programs similar to MasterCard or Visa. Through adopting this incompatible model of Bitcoin, customers would successfully hardfork, or make legitimate, prior to now invalid blocks and transactions which in the long run forces everybody to improve their purchasers in a similar fashion — else risking network stability and replay attacks.
Bitcoin’s writer, the nameless Satoshi Nakamoto, had lengthy since stepped clear of Bitcoin when this debatable mission was once introduced and the neighborhood was once left to decipher Satoshi’s comments for steerage as although they have been sacred writ. Bitcoin XT failed to realize consensus because it naively proposed expanding the utmost blocksize and its proponents sought to subvert consumer consensus thru closed-door, developer-miner-corporation collusion. With out coming into each minute element of the notorious “blocksize war” and spawning an entire book, we will it seems that apply from the extensive two-year squabble the crucial serve as of complete nodes (customers) coordinating to put in force new laws with out fortify from miners by the use of user-activated softforks (UASF).
Had Bitcoin fallen into the large block lure, community decentralization and Bitcoin’s apolitical nature would have suffered accordingly. To know the ramifications of fixing a apparently easy variable, that being the blocksize prohibit, calls for now not most effective figuring out the technical have an effect on at the codebase integrity, but in addition hidden consequences inviting further assault vectors towards the nascent community ecosystem. One can prolong this line of pondering towards lately’s asinine suggestions of transferring Bitcoin to proof-of-stake in lieu of proof-of-work. Although the option to the blocksize conflict was once resolved technically thru a UASF, the social drama that ensued required non-technical answers of merely last company and now not budging on a adverse tool implementation, regardless of the company or superstar developer backing.
Assaults Through BIP Activation Way
Dashjr contends an assault at the Bitcoin Core building procedure took place simply ultimate 12 months: the “Speedy Trial” activation manner of the much-anticipated “Taproot” softfork improve (BIP 343). The Fast Trial good judgment works to turn on a BIP implementation with out the chance of an unwanted chain break up by way of both temporarily succeeding or temporarily failing to turn on inside a three-month time-frame. As soon as the paintings to construct Taproot was once finalized, the builders may just now not come to common settlement at the activation manner and necessarily neglected the an important step of first receiving undoubtable neighborhood consensus.
Even though Taproot effectively activated and the next options supplied have been undoubtedly recommended for customers, its activation manner was once perceived as debatable and posed attainable vectors of assault whilst environment deficient priority for long term BIP activations. The Fast Trial activation mechanism was once observed as an assault at the Bitcoin Core building procedure as a result of some builders stepped clear of the perceived neighborhood consensus whilst refusing to imagine BIP 8 as an activation manner, in a different way referred to as the “Let’s see what happens” proposal, within the deployment of Taproot.
The Fast Trial manner was once antithetical to the blocksize conflict consequence, the place the feud concluded that customers coordinating near-unanimous settlement must regulate the community consensus laws and now not the miners. With Fast Trial and with out BIP 8, the verdict to turn on (or now not turn on by way of simply now not signaling when it is deployed) fully depended at the miners regardless of consumer consensus. The arguably reckless Fast Trial deployment manner went towards perceived neighborhood consensus and, to mitigate this in long term, would doubtlessly require coordination of a UASF with sufficient viable adoption past a couple of involved other people within the nook of a room to counter a BIP’s activation.
The panelists at “Fighting Assaults On Bitcoin” thought to be the right way to assess those ancient assaults and steer clear of equivalent assaults in long term. The “attackers” pushing for Bitcoin XT or Fast Trial won’t have had malicious intent with their proposals, but obviously their strategies conflicted with sure rules which a portion of the neighborhood adamantly defends — this is, the customers have the only proper to approve or veto adjustments to the consensus laws. In hindsight, the attackers merely didn’t apply the similar rules of Bitcoin that the neighborhood did, which led to the ones assaults turning into a subjectively interpretive conflict of what was once “perfect” for Bitcoin.
The aforementioned Bitcoin XT and Fast Trial eventualities put across the strategies during which Bitcoin Core’s building procedure may well be made debatable, emphasizing the need to method all BIP implementations cautiously and thoughtfully. Within the following sections, the panelists theorize further believable assault vectors.
Bitcoin Instrument Verification Assaults
Bishop’s pursuits within the building procedure come with deterministic builds and construct signing which will also be leveraged to forestall sure assault vectors on Bitcoin customers, particularly assaults that search to idiot the consumer into believing they’ve downloaded a bona fide Bitcoin Core consumer.
Somebody who’s a consumer of a Bitcoin consumer should obtain it from someplace at the spam-ridden web. If the webpage website hosting the obtain record is compromised or intercepted all the way through obtain, then the record itself can have been maliciously changed. How can that consumer end up the model they downloaded is certainly the meant Bitcoin consumer?
The average manner to supply non-repudiation of a tool construct, or evidence of the integrity and beginning of the knowledge, is with digital signatures. Virtual signatures, the tamper-proof wax seal’s digital and mathematically-inclined cousin, are an ordinary part of maximum cryptographic protocols the usage of asymmetric (private and non-private) keys to allow authentication between two strangers — however wait! This doesn’t ensure signature authenticity. In the end, authentication with out self assurance within the keys used to ensure the signature is needless because the recipient should be confident the verification key in reality belongs to the sender.
There’s then some other sly assault vector if the verification tool itself is compromised. A artful prison claiming to be somebody who they don’t seem to be, however having to additionally end up their declare thru a virtual signature, may just plant the compromised key-verifying tool for the unsuspecting consumer to obtain and because of this be offered with a false results of authentication. The compromised tool accommodates an overly delicate malicious program that, at a snappy look of the code, would manipulate the consumer into reasoning the verification tool yielded a correct end result.
Whilst deterministic builds don’t resolve authentication of virtual signature ownership, it does paintings to cut back the consider required in one supply or declare to the tool a consumer has downloaded. Deterministic builds paintings to offer protection to the tool implementation towards a pair rogue builders or a compromised developer’s keys all the way through the improvement procedure. This coverage is accomplished thru cryptographic hashes of the tool that builders digitally signal because the tool is constructed all the way through every step of the construct procedure — successfully making sure that the general tool binary files are the similar because the binary recordsdata that the fair builders constructed and due to this fact hasn’t been compromised in any shape or style.
Altogether, with deterministic builds and construct signing, one can mainly hint consider within the tool from the binaries to the supply code to the git commits made by way of quite a lot of builders and establish what adjustments have been offered by way of whom. The legitimacy of the tool can then be additional investigated thru tactics like web of trust the place customers can arbitrate whether or not or now not the keys being verified are unique and they’re running the meant Bitcoin consumer. Subsequently, with out profiting from deterministic builds and construct signing, the consumer is vulnerable to a myriad of assault vectors.
One such instance: if a consumer downloads a Bitcoin consumer thru HTTP in lieu of HTTPS with a public Wi-Fi connection, in all probability at a overseas espresso store or lodge, whilst now not verifying the construct signing, then attackers may just really well intercept the consumer’s obtain connection and change the obtain record with a villainous model of Bitcoin that can scouse borrow cash, secret agent on customers, or carry out different damaging purposes.
Bishop unearths {that a} “a laugh” a part of the tool development procedure is keeping up constant building atmosphere variables which paintings to get rid of any assets of non-determinism. Non-deterministic assets may just lead to unwanted variabilities of the construct signing because of the naturally open atmosphere builders are development on. A variability, like differing running programs between person builders, generates a wholly other hash on the finish of the improvement procedure. Preferably, doing away with all assets of variability within the construct atmosphere would make stronger deterministic builds and therefore make stronger consider of their integrity.
Planned Ossification Of Bitcoin Construction
Lopp, channeling his inside Solar Tzu, devises a in particular devious manner of dividing and manipulating Bitcoin Core à l. a. nefarious developer(s) sowing discontent during the neighborhood and GitHub repositories. If a reputable developer have been to put across excessive inflammation and anger in opposition to any and all protocol enhancements, patches or adjustments, then the rising common consensus will likely be one in every of concern in opposition to touching the protocol. This “freezing” of the improvement procedure is referred to as ossification and would make endured protocol enhancements nearly inconceivable.
Possibly attaining ossification is in the long run recommended for the protocol since this could suggest Bitcoin’s standard established dominance, but Lopp argues simply the other in that ossification is an exploitable assault vector somewhat than an efficient protection. Whilst ossification works to protect towards adverse adjustments to the Bitcoin protocol, similar to Bitcoin XT, it would additionally paintings to forestall recommended or important updates that offer larger peer-to-peer privateness and extra powerful codebase enhancements.
The assault vector Lopp describes can be extraordinarily tricky to evaluate at the spot whether or not an lively war of words within the building procedure is an assault at the protocol or a legitimately positive war of words. This speaks to the former level the place, in hindsight, the assault is a lot more visual after the reality. With out possessing overall omniscience of every developer’s true intent, the improvement procedure can be caught between a rock and a troublesome position.
Protection towards technical assaults, just like the above-mentioned early insects and oversights, are moderately simple and logical of their answer. When introducing the erratic, human part, then again, we start enjoying a deadly recreation with some distance much less predictability. Socially-engineered assaults are incessantly packaged with fuzzy answers and can most probably should be handled as they arrive. A centered memetic or mainstream narrative assault will also be fully inconspicuous and figuring out a protection towards them is in large part a grey space.
War is the philosophy of deception. Arguably, essentially the most logical assault vector for would-be adversaries may well be to incite social discontent and meme warfare. Lopp explains that intentionally forcing ossification is the easiest assault as a result of many customers would imagine it a protection.
Judicial Assaults On Bitcoin Core Builders
The continuing incidence of Craig Wright, a person claiming to be the nameless Satoshi Nakamoto, and his cryptographic antics plus judicial intimidation of Bitcoin Core builders represents an instantaneous assault at the Bitcoin Core building procedure. Regardless of the mounting evidence that Craig Wright isn’t Satoshi Nakamoto, he continues to wreak havoc by way of racking up hundreds of thousands of bucks in criminal charges and successfully outbidding the protection on account of the astronomical prices — monetary and private — that Craig Wright imposes on volunteer builders and participants by the use of Strategic Lawsuits Against Public Participation (SLAPP fits). Recall the artful prison claiming to be somebody who they don’t seem to be, however having to additionally end up their declare thru a virtual signature; this exact scenario played out however, because of the abstruse nature of uneven cryptography, has been useless in convincing the judicial device.
As a result, Bitcoin Core builders must undertake nameless contribution strategies or chance being centered by way of a pricey and burdensome litigation procedure. Those strategies of anonymity in the long run rely at the person’s privateness practices, in all probability similar to warding off Bitcoin 2022 and meetings fully to handle anonymity. But litigation against a supposedly anonymous individual could still be possible if there may be an IRL title or personally-identifying part tied to that developer’s pseudonym. On the other hand, the will for contributing privately is itself a gift and long term burden on builders and their households.
Ultimately, if those judicial assaults on Bitcoin Core participants persist or Jack Dorsey’s Bitcoin Legal Defense Fund runs dry, builders will likely be driven out of the distance and extra escalate protocol ossification since burning cash in never-ending litigation isn’t very sexy; a “dying by way of 1000 cuts,” as Shinobi eloquently summarized it.
Long term Assaults And Headaches In Bitcoin Construction
If Bitcoin is predicted to live to tell the tale and thrive now not simply on this century, however for lots of centuries and so forth, then cautious steps should be taken in formulating protection mechanisms towards anticipated and surprising assaults on Bitcoin Core in addition to the Bitcoin ecosystem. You’ll’t have a multi-generational wealth car if it turns into nugatory ahead of you die.
Whilst the panelists held differing perspectives on whether or not attacking Bitcoin customers is an identical to attacking the Bitcoin protocol, there live to tell the tale vectors of assault at the customers, just like the aforementioned fraudulent virtual signatures and the continuing Craig Wright criminal saga. Different vectors come with deficient pockets construct practices or malicious mainstream narratives brainwashing customers which may be considerably adverse to sure rules of Bitcoin we discover paramount.
Despite developments in Bitcoin non-public key control, referred to as wallets, there stays the potential of dangerous actors deliberately development wallets that don’t apply the newest nor ideally suited security practices out there to them. For example, there are nonetheless pockets implementations that use a single address to send and receive bitcoin — thus exposing any privateness customers can have.
As nicely, even supposing now not essentially intentional however somewhat a results of its obstacles, any roughly mild pockets (one that doesn’t additionally perform as a complete node itself) calls for a connection to a complete node in an effort to keep in touch transactions. Mild wallets, in particular widespread for informal customers, pose the duality of a easy, easy-to-use interface, but in addition provide gaps in safety ripe for assault vectors. Customers of those wallets are vulnerable to their transaction communications being intercepted by way of doubtlessly nefarious actors. An easy answer — however impractical for some — to this vector can be to forego the usage of mild wallets in prefer of complete node wallets.
Shinobi envisions choice assault vectors stemming from undeniable disinformation campaigns towards Bitcoin after which temporarily spiraling into govt lobbying for criminal motion and heavy laws. One such glaring disinformation marketing campaign is the unfounded perception that proof-of-stake is a viable choice to proof-of-work. If all jurisdictions, basically the ones with readily reasonable and considerable power infrastructure, fell in a domino-effect of energy grabbing desperation to curb stomp Bitcoin thru outright banishment of bitcoin mining, in all probability enforced by the use of inspecting unique energy grid power modulations that may establish bitcoin mining rigs, then relocating all of the current hash energy off-grid would end up relatively difficult.
The method of changing and buying the important scales of power off-grid — in particular in secret — is not any smooth job. For example, sun panels and wind generators stay some distance too restrictive to behave as an an identical exchange and completely shoulder a network-wide transition to off-grid bitcoin mining because of sun and wind’s inherent variable and intermittent energy technology. Dashjr proposed a possible answer by way of deviating from the present proof-of-work same old provided that the location have been dire sufficient. If the blockchain have been halted from some unattainable political dictation or the hashing set of rules (SHA256) used to safe Bitcoin have been damaged, then coming in combination to discover a answer could also be imaginable and can be recommended for all community individuals.
This proposal of editing proof-of-work as we are aware of it is itself a case-in-point for the surprising assaults that might happen on Bitcoin and the inevitably debatable selections in the course of the Bitcoin Core building procedure that will apply given one of these dire situation.
Proceeding down the trail of hypothetical eventualities that will require time-sensitive BIP implementations, in all probability the worst-case situation conceivable can be if the SHA256, RIPEMD-160, or ECDSA mechanisms have been without a doubt compromised — however even then, the query stays of what can be viable choices? Lopp jokes in pronouncing a quantum-proof set of rules will make everyone glad, however this cheeky reaction will most probably change into truth in the future within the some distance long term, necessitating unsavory arduous fork discussions round sensible protection mechanisms towards quantum computing exploiting asymmetric cryptography.
Bitcoin is an apolitical cash and non violent protest towards the incumbent and corrupt financial regime. On account of the character of the opponent Bitcoin is going through, i.e., the U.S. buck, an unrelenting barrage of technical and social assaults towards Bitcoin is prone to happen, if not already under way. Bishop relates Bitcoin’s fully voluntary neighborhood, who’s steadfastly protecting Bitcoin on the able, to that of a self-developed “immune device” which may be Bitcoin’s biggest defensive and offensive mechanism.
Final Ideas
In abstract, Bitcoin is by no means invincible. With out actively making an allowance for all attainable assault vectors and looking for respective answers, the always-waiting adversaries may just in finding weaknesses within the code or locally itself. Whether or not the assault be from colluding events, counterfeit Bitcoin tool, planned ossification, centered assaults in the course of the judicial device or some unknown long term crisis situation, Bitcoiners should paintings in combination and unite to seal any gaps which may be the start of the top for Bitcoin.
The purpose of this panel isn’t to instill within the target market doom nor gloom, however somewhat to prescribe a correct dose of truth with the very imaginable assaults Bitcoin building and the community may just come across shifting ahead. Ignoring this could be extremely adverse to the whole safety of Bitcoin if we make a decision to reside in comfortable lack of awareness of those assault vectors. Must historical past have anything else to show us, it might be that each one current and former financial regimes — outdoor of Bitcoin — have succumbed to the fallibility of human establishments. Let’s paintings not to have Bitcoin enjoy a equivalent destiny.
People are rationally pushed by way of financial incentives which has enabled the open supply, pseudo nameless, financial nature of Bitcoin to harness a big, professional crew of hackers with alternative for a praise of the scarce foreign money this is bitcoin. The invention and exploitation of flaws that might compromise Bitcoin would satirically diminish the attacker’s newfound wealth — thereby, in principle, monetarily encouraging hackers to repeatedly fortify the Bitcoin community and responsibly document insects and exploits.
Regardless of discussions of the way to assault the Bitcoin Core building procedure and the broader ecosystem with little readily-available answers of the right way to precisely verify and save you those assaults, Bishop ended the panel with a poignant commentary that spoke to the best incentive of all: cash. He remarked, “Bitcoin is the best malicious program bounty program of all time … excellent success.”
This can be a visitor submit by way of Okada. Evaluations expressed are fully their very own and don’t essentially replicate the ones of BTC, Inc. or Bitcoin Mag.








![Methods to Purchase DeFi Pulse Index on CoinStats [The Ultimate Guide 2022]](https://bitrrency.com/wp-content/uploads/2022/05/DeFi_Pulse_og-100x70.png)

